Recover Perl from an EXE
Some time ago, during one of my Red Team exercises, I came across a Perl in the form of a Windows executable. This one is used to perform a series of operations against the domain and in order to authenticate it seems to generate credentials in memory from an encrypted key file. How can I get those credentials back?
One way might have been to mount a fake Responder-style domain controller. But… Why make it easy? Also, I was curious to find out what encryption method is used, in case I would find something similar later on during the pentest.
Executable analysis
A brief analysis with strings shows us that it is a Perl script packed in an EXE executable. In particular, it appears that ActiveState PerlApp was used for this purpose.
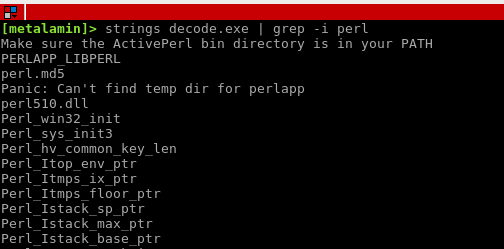
So far all the Perl to EXE packers I have found have to save the script clearly before they can launch the interpreter. In some cases they are stored in a file and in others they remain in memory. In the sample we’re interested in, he unpacks it in memory. Let’s look at a way to retrieve it using OllyDbg.
Recovering the Perl
We load the executable into OllyDbg. But before launching the execution we will put a breakpoint somewhere after the script is loaded. To do this we first show the text strings.
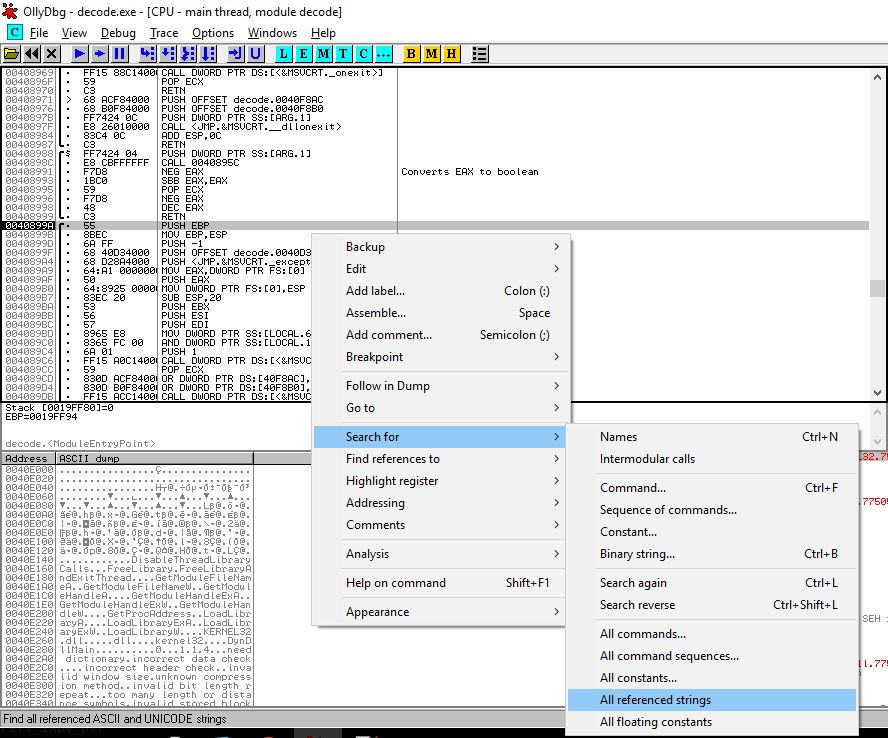

We know that after unpacking the script, the executable has to mount the string for the Perl interpreter call. Let’s look for strings that look like arguments for launching the Perl interpreter and stop the execution at that point. We choose some of the chains and set the breakpoint by pressing F2.
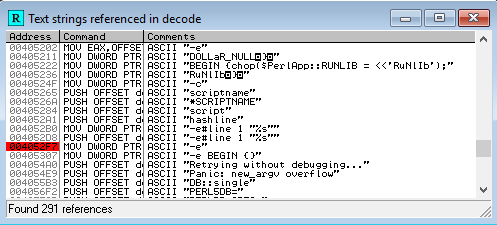
We are now ready to start the program by pressing F9.
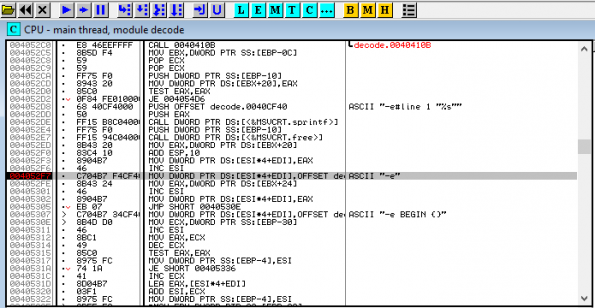
Once we have stopped at our breakpoint, we open the Memory Map by pressing “Alt+M”.
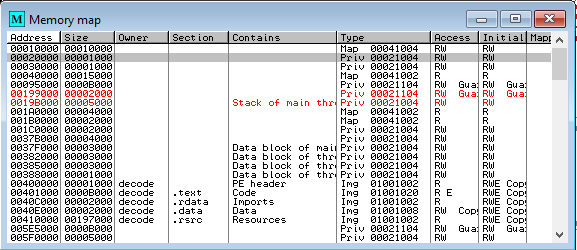
With the memory window open we do a search (Ctrl+B) for strings that can contain the script we are looking for. For example, calls to perl libraries that begin with “use” (note the space at the end).
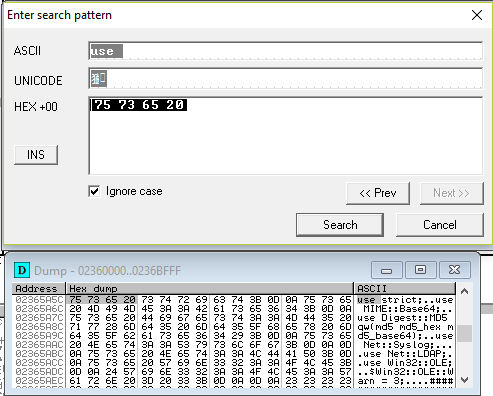
We already got the script in memory and we know where it is. All we have to do is save this memory segment in a file and store the script.
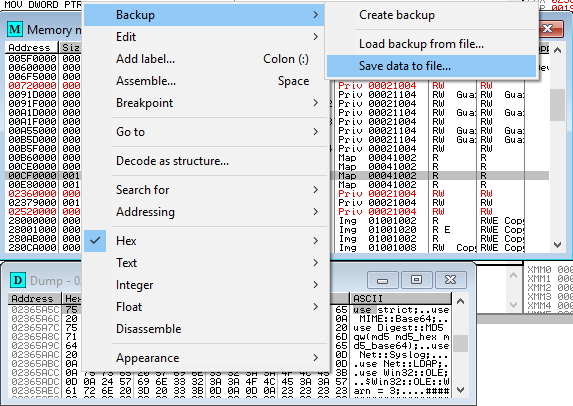
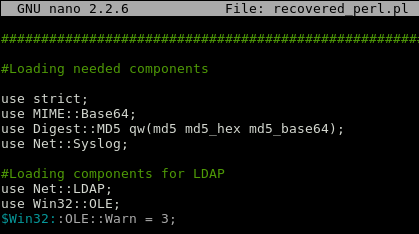
And with this we have recovered the entire script including the programmer’s comments.
Surely we could have done it more elegantly or more quickly, but this is the one I thought of at the time and wanted to share.
